Webhosting – External Web Sites Not Accessible from Internal Network
Had to host a website on my home server. With the latest ATT UVersion fiber 1GB symmetric and latest router BGW210-700 (2019 version), and latest software on USG, you would imaging it would be done in a few hours.
As it turns out it’s wasn’t as easy as it appears.
Here are two options to setup the web hosting:
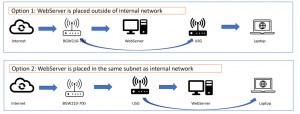
Configuration wise, given those options, you may choose different strategy to router traffic from internet to the web servers. Let’s evaluate each of the configurations:
- Options 1: Web server is placed in the DMZ, and your internal clients are served by USG.
- Option 1A: Port forwarding on ATT UVerse router BGW210 to forward any external traffic to the web server, port 80 (and 443 if https is also enabled): Steps:
- go to http://192.168.1.254, enter Access Code listed on your device’s side panel
- Nat/Gaming menu
- Add new “Custom Service” with name something like “webhosting”, specify port 80
- Assign the service to the dedicated web server
- Option 1B: IP Passthrough, and “IP Passthrough” Mode allocation method on ATT UVerse router to pass all traffic to the web server
- IP Passthrough Tab
- Select IP Passthrough as the Allocation Mode
- Select DHCPS-Fixed
- Choose the MAC address of the web server. Then Save
- Option 1C: IP Passthrough, and “Default Server” Mode allocation method on ATT UVerse router to pass all traffic to the web server
- Select Default Server as the Allocation Mode
- Select Web Server as the Internal Server IP Address
- Then Save
- Option 1A: Port forwarding on ATT UVerse router BGW210 to forward any external traffic to the web server, port 80 (and 443 if https is also enabled): Steps:
If you follow along correctly, with Options 1A, 1B and 1C, the external users could have access to the web server as expected. However, there is an issue for the internal user behind the USG network. Users will not have access to the web servers, as the ATT UVerse router only understands to router “external” traffic to the web servers. If the traffic was originated from internal network, it does not re-router the traffic as expected. You will see the web connection eventually times out.
- Option 2: Web server placed in the same VLAN behind the USG.
- Option 2A: Double SNATTING.
- Setup Port Forwarding on BGW210 for port 80 to the USG device, similar to Option 1A, but select USG as the destination server
- Setup Port Forwarding on Unifi Security Gateway to forward external traffic to Web Server
- Option 2B: IP PassThrough on ATT Router and Port Forwarding on USG
- Setup the IP PassThrough to USG device on the ATT Uverse, similar to Option 1C, but select USG as the Internal IP Address.
- Setup Port Forwarding on Unifi Security Gateway, to forward external traffic to web server
- Option 2A: Double SNATTING.
For Option 2A, you can access the web sites from external network IP addresses. But you can’t access to the web site from internal network computers or clients. It’s much the same way as the Option 1A, 1B, 1C.
The only option that’s working completely, is the Option 2B. Either external or internal clients could access the web sites without any connectivity issue.
Important: Any time you make a change on UVerse Router, you will need to reboot to make sure it takes effect. Same goes for the USG device. Otherwise, you may see intermittent connectivity issues and will confuse your configuration verifications.
For those cases that you could not access the site from internal network, there is a not so elegant work around. You can add the internal web server’s ip address to the local laptop’s hosts file such that instructing the laptop/client to find server locally instead of using external DNS to resolve the external IP address of the site. This is super troublesome if you have lots of clients that you need to update. It’s a nightmare to manage.
What happened and Why?
In general, ATT’s router BGW210 (and similar) does not support a feature called “NAT loopback”, or sometimes called with other terms, like, “NAT Hairpin”, “NAT Reflection”. When an internal originated traffic hits the BGW it does not understand it needs to deal with it differently.
USG, on the other hand, natively supports NAT Loopback by default. You do not even need to manually turned it on.
The reason it didn’t work on Option 2A, is that, because of the double SNATTING, the USG does not have the ISP’s internet IP bound to the USG, it does not know it needs to distinguish between internal vs external traffic. Essentially, USG treats itself as an internal device, as it derives an local IP address from ATT router by itself in the network topology.
In the case of Option 2B, however, because of the IP Passthrough, the ISP’s external IP address is bound to the USG, it knows to distinguish between external vs internal traffic. Hence the NAT Loopback feature kicks in when dealing with internal traffic – it just hands out an internal web server ip address to the clint to connect. What a wonderful world!
Of course, IP Passthrough + NAT Loopback is not the only solution to address these issue in the network world. You could setup a separate internal DNS server to just indicate the local ip address for those sites. This is very much the same concept of setting up Hosts file, except it’s done in the network level not on the client machine separately. Another solution is to acquire more sophistic network management gears that supports “DNS Doctoring”.
Until next time, happy hosting!




Recent Comments